(Updated: August 16, 2015)
In July and September of last year, the Brazilian weekly television magazine Fantástico broadcasted news reports about NSA operations, while showing a series of slides from an unpublished NSA powerpoint presentation in the background.
The slides seem to be about NSA's corporate partners for the "collection of communications on fiber cables and infrastructure as data flows past" - which became known as "Upstream collection", a term mentioned in one of the PRISM-slides.
The corporate partnerships are one of three ways NSA is intercepting the world's main internet cables:
- Cooperation with telecommunication companies
- Cooperation with foreign intelligence agencies
- Unilateral cable tapping operations
On twitter, Glenn Greenwald once said that these slides would also be published and explained separately, but so far this hasn't happened - that's why it's done here.
UPDATE:
Almost two years after these slides were shown on Brazilian television, the full NSA presentations to which some of them belong were finally published, as part of a report by The New York Times and Pro Publica from August 15, 2015.
> See: FAIRVIEW: Collecting foreign intelligence inside the US
-----O-----
The first series of slides was shown in a Fantástico report from September 8, 2013. These slides are posted here in the order in which they were seen in the report, which might be the order of the original NSA powerpoint presentation.
The slides show the logos of the National Security Agency (top left) and its Special Source Operations (SSO) division (top right). They are marked TOP SECRET // COMINT // NOFORN, which means they are classified Top Secret, in the compartment for Special (Signals) Intelligence and that it's not allowed to distribute them to foreigners, not even to the Five Eyes partners.
Probably one of the first slides of the presentation shows a map of "optical fibre submarine networks", which was prepared by the telecommunications company Alcatel Lucent in 2007. Based upon dates in some of the slides, this NSA presentation seems to be from late 2011 or early 2012.
The Corporate Portfolio of collection programs in which SSO is cooperating with corporate partners is listed in the following slide. It is assumed that FAIRVIEW, BLARNEY and STORMBREW are for collection within the US and the programs under the OAKSTAR umbrella are intercept facilities elsewhere in the world. Two programs seem to be conducted by SSO in cooperation with TAO, which is NSA's computer hacking division:
The next slide is about the Transit Authority, which is the most mysterious of the four legal authorities that govern NSA operations. Until now, it's not clear what the legal basis of the Transit Authority is. One option is a secret presidential directive signed by Bill Clinton or George W. Bush, another option is that this method was authorized by the FISA court.
Transit Authority applies when both ends of a communication are foreign, which is checked by filters at the front-end collection systems. When the TOPI (Target Office of Primary Interest, a unit that conducts the data analysis) discovers that accidently one end of the communication is in the US, the SSO Corp Team has to be informed, which reports to the Oversight and Compliance unit (NSA/SV):
The Transit Authority is illustrated in the next slide. With a close look one can see there's a star placed between Iran and Iraq, one in the US and one somewhere near French Guyana. There's an elliptical line connecting them, as an example of communications traffic from Iran to Guyana, which transits the United States:
Some "unique aspects" of the upstream collection are that it takes place under various legal authorizations:
- Executive Order 12333: for collection outside the US
- Transit: for collection within the US, with both ends foreign
- FISA: for collection within the US, with one end foreign and targets approved individually by the FISA Court
- FAA: for collection within the US, with one end foreign and a list of targets approved anually by the FISA Court
Under section 702 FAA, NSA is also collecting data from internet service providers under the PRISM program. From a 2011 FISA Court ruling (pdf) that was declassified upon request of the Electronic Frontier Foundation we learn that under section 702 FAA, NSA acquires more than 250 million "internet communications" each year. This number breaks down as follows:
- Upstream: ca. 9% or more than 22 million communications *The ruling doesn't explain what exactly a "internet communication" is. A problem that troubled both NSA and the FISA court was that under Upstream it's technically very difficult to distinguish between single communications to, from or about targeted persons and those containing multiple communications, not all of which may be to, from or about approved targeted addresses. The latter may contain to up to 10,000 domestic communications each year.*
- PRISM: ca. 91% or more than 227 million communications
The actual intercept facilities are probably located at sites of telecommunication companies or collection is done with their assistance.
There are delays between the tasking, which is when an analyst orders particular information to be collected, and the actual collection of those data.
The following slides show details of a number of different programs involved in the Upstream collection. For each program there's the SIGINT Activity Designator (SIGAD), the Producer Designator Digraph (PDDG), the legal authority, what is collected, the key targets and in some cases a custom logo for the program. There are no slides with details about DARKTHUNDER, STEELFLAUTA, ORANGEBLOSSOM, BLUEZEPHYR and COBALTFALCON.
SILVERZEPHYR is for collecting internet content and metadata under FAA authority, and telephony content and metadata under Transit Authority, focussed on South, Central and Latin America. As the program operates under Transit Authority, the intercept facility is most likely located in the US. The corporate partner is codenamed STEELKNIGHT:
YACHTSHOP is for collecting worldwide internet metadata, which are stored in the MARINA database. Probably the program operates under EO 12333 authority and the corporate partner, codenamed BLUEANCHOR, is outside the US:
ORANGECRUSH was not active at the time of the presentation, but was intended to collect internet and telephony content and metadata at an intercept facility outside the US in cooperation with a corporate partner codenamed PRIMECANE and a 3rd Party partner agency.
Update:
According to the book 'Der NSA-Komplex' by Spiegel journalists Marcel Rosenbach and Holger Stark, ORANGECRUSH is a cooperation with an American high-tech company and a Polish intelligence agency to collect metadata and content related to the Middle East and Afghanistan from fiber optic cables in Europe. This means PRIMECANE is the cover name of this American tech company and confirms that Poland is a 3rd Party partner of NSA.
SHIFTINGSHADOW is for collecting telephony content and metadata from the telecommunications providers MTN Afghanistan, Roshan GSM and Afghan Wireless Communication Company (AWCC). This is done through an intercept facility which is probably in or near Afghanistan. It seems NSA is not cooperating with these Afghan telecom providers, hence they wouldn't be named openly in this slide:
MONKEYROCKET is for collecting internet metadata and content focussed on counter-terrorism in het Middle East, Europe and Asia. The collection takes place at an intercept facility outside the US and is therefore authorized under EO 12333:
There are also a number of programs and partners for collection of both internet and telephony data under FAA authority. They are designated by a SIGAD in the format US-984X*. From another source we know that there are:
- Eight facilities under STORMBREW (US-984XA-H)As this is under FAA authority, the intercept facilities and corporate partners are in the United States. Maybe some of these partners are the ones with the codenames WOLFPOINT, ARTIFICE, LITHIUM, SERENADE and STEELKNIGHT, which are mentioned in other documents.
- Two facilities under FAIRVIEW (US-984XR and US-984X2)
- Nine companies cooperating in the PRISM program (US-984XN)
The next slide shows a bar chart with green bars for sources where the SSO division uses arrangements with corporate partners, and blue bars for sources where there are no such arrangements needed, which means SSO can collect the data on its own. From the most to the least productive source, the bars represent:
- US-984X*: Programs under FAA authority
- US-990: FAIRVIEW (Transit authority only)
- US-3237: SMOKYSINK
- USJ-751: ?
- US-3167: SARATOGA
- US-3171: DANCINGOASIS
- US-3310BG: SCALAWAG
- US-3180: SPINNERET
- US-984: BLARNEY under FISA authority
- USJ-799: LADYLOVE (the satellite station in Misawa, Japan)
BLARNEY is for collecting telephony and internet data under FISA authority, which means a FISA Court order is needed. Main targets are foreign diplomats and governments, terrorists and economic targets. As collection is under FISA authority, the intercept facility is in the US. According to the Wall Street Journal and confirmed by Marc Ambinder, BLARNEY stands for cooperation with AT&T.
MADCAPOCELOT is for collecting internet content and metadata focussed on Russia and European counter-terrorism. Collected data are processed and analysed by XKEYSCORE with metadata being stored in MARINA and content in PINWALE. As the program is operating under EO 12333, the intercept facility must be outside the US. For reasons unknown, MADCAPOCELOT is closely related to the STORMBREW program.
For the STORMBREW program a map shows a line marked as OC-3, which runs across the United States. OC-3 is a network line with a transmission data rate of up to 155.52 Mbit/s using fiber optics. This is too low for being a regional, let alone a national backbone link, so the blue line does not represent an intercepted internet backbone. The cable connects eight locations marked with a green dot, one with a grey dot, one with a sun symbol and one marked as "Site C":
UPDATE:
The meaning of this map was claryfied by a new slide from a different NSA presentation, which was disclosed in Glenn Greenwald's book 'No Place To Hide' on May 13, 2014. It shows seven international choke points of telecommunication cables that serve as access points for the STORMBREW collection program:
- BRECKENRIDGEIn the book, Greenwald lists an additional site called QUAILCREEK. These cover names are real names of holiday and ski resorts, some of them actually even near the dots on the map. These locations correspond to the green dots in the previous slide, so the OC-3 cable in that map most likely connects these various collection sites to transfer the data to a central location. The grey dot might then be an intercept site that is not active yet/anymore and "Site C" maybe the location where the centralized "Collection" takes place.
- TAHOE
- SUNVALLEY
- WHISTLER
- MAVERICK
- COPPERMOUNTAIN
- KILLINGTON
STORMBREW is for collecting internet data under FISA and FAA authority and telephony data according to a certain directory. With collection being authorized under FISA and FAA, the interception takes place in cooperation with a major US telecommunications provider with access to international cables, routers and switches. According to NSA historian Matthew Aid, the provider codenamed STORMBREW is Verizon.
FAIRVIEW is for collecting internet and telephony data and is a "key corporate partner with access to international cables, routers and switches" just like STORMBREW. The slide below was published in 'No Place To Hide' but with the bottom part removed. From a similar presentation we know that there it says that under FAIRVIEW, internet collection is limited to "port 25 collection", which means e-mail, and telephony collection uses the mysterious "Directory ONMR". Slides from this other presentation will be posted on this weblog separately.
For the FAIRVIEW program there's also a map, but this one shows a large number of many different markers with no lines or cables between them. At the moment it isn't clear how to interpret this:
Former NSA official Thomas Drake told DailyDot.com that FAIRVIEW is a highly classified program for tapping into the world’s intercontinental fiber-optic cables. It's an "umbrella program" with other programs underneath it. One of them is BLARNEY, which accesses internet data at key junctions and is facilitated by arrangements with commercial cable companies and internet service providers.
-----O-----
According to The Guardian, the real names of the corporate partners mentioned in various of these slides are so sensitive that they are classified as Exceptionally Controlled Information (ECI), which is "a higher classification level than the Snowden documents cover", thereby suggesting that he had no access to that kind of information - although a regional German paper was able to publish the real names of seven major submarine cable companies (but they had GCHQ covernames).
In the Upstream slides we see partners codenamed STEELKNIGHT, BLUEANCHOR and PRIMECANE. In other documents, WOLFPOINT, ARTIFICE, LITHIUM and SERENADE are also mentioned as covernames for corporate partners. Most likely all four are American companies.
-----O-----
Another series of slides was shown in a Fantástico report from July 9, 2013. Maybe they are from another presentation, but because they have the same layout and are also about "upstream collection" it's also possible they belong to the series posted above.
This series contain a number of maps, which, according to Brazilian media, show the amount of exchanged messages and phone calls (although actually DNI only refers to internet traffic) by various countries in the world with North Korea, Russia, Pakistan and Iran on March 4-5, 2012.
In the first slide we see internet traffic to Pakistan, which is eligible for collection under Transit authority:
The slide below has a map showing the internet traffic to Pakistan, which is eligible for collection under FAA authority:
The next slide shows a list of "Top 20 Pakistani domains (.pk)" which where tracked between February 15, 2012 and March 11, 2012:
A map representing "1 Day view of authorized (FAA ONLY) DNI traffic volumes to North Korea within FAIRVIEW environment", which means internet traffic which is eligible for collection under FAA authority:
Next is a list op "Top 20 North Korean domains (.kp)" which where tracked between February 15, 2012 and March 11, 2012. Note that only two websites generate notable traffic, all other have less than 1 Kbps:
A map showing internet traffic to Iran, which is eligible for collection under FAA authority:
A map showing internet traffic to Russia, which is eligible for collection under Transit authority:
The following slide says the collection programs in which Special Source Operations (SSO) cooperates with corporate parters, contributed to 1230 reports of NSA's Counter Foreign Intelligence Product Line (S2D). As this represented circa 29%, this product line produced a total of some 4240 reports in 2011:
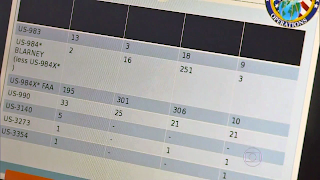
The next slide shows a table with the headers and/or some of the top rows apparently blacked out, so we can only see a list of some programs and a range of numbers without knowing what they stand for. The SIGADs at the left designate the following programs:
- US-983: STORMBREWAlthough we don't know what the numbers stand for, it's clear that the programs under FAA authority (which also include PRISM) are by far the most productive ones:
- US-984*: BLARNEY under FISA authority
- US-984X*: Programs under FAA authority
- US-990: FAIRVIEW
- US-3140: MADCAPOCELOT
- US-3273: SILVERZEPHYR
- US-3354: COBALTFALCON
Probably one of the final slides provides contact information: first the names/e-mail aliasses of the collection managers for the FAIRVIEW, STORMBREW, BLARNEY, OAKSTAR, and MADCAPOCELOT programs. Brazilian television showed this slide uncensored with the names visible, but here we blacked them out. Under "Mission Management" is an e-mail address (in the strange format NSA uses for internal messages) for contacting the SSO corporate program mission management and finally there are keywords for finding out more information on NSA's intranet and the NOFORN-Wiki:
Update:
An article in the French paper Le Monde from May 8, 2014 lists a number of targets of the Upstream collection method during a month in 2013. These targets included the vice president of the Philippines Jejomar Binay; the interior minister of that country Manuel Roxas; the Ensenada Resort & Convention Center in Tela, Honduras; the International Centre for Theoretical Physics (ICTP) in Trieste, Italy; the American att.net and the Austrian chello.at e-mail domains, as well as the stc.com.sa top-level domain of the Saudi Telecom Company. Finally the Pakistani IT security firm Tranchulas and the Lybian International Telecom Company were mentioned as being targets of NSA.
UPDATE:
Almost two years after these slides were shown on Brazilian television, the full NSA presentations to which some of them belong were finally published, as part of a report by The New York Times and Pro Publica from August 15, 2015.
> See: FAIRVIEW: Collecting foreign intelligence inside the US
Links and Sources
- PCLOB.gov: Section 702 Program Report (pdf)
- DNI.gov: NSA's Implementation of Foreign Intelligence Surveillance Act Section 702 (pdf)
- Wikipedia: Upstream collection
- EmptyWheel.net: Federated Queries and EO 12333 FISC Workaround
- DailyDot.com: Forget PRISM: FAIRVIEW is the NSA's project to "own the Internet"
- The Guardian: Snowden document reveals key role of companies in NSA data collection
(credits for providing the video footage go to @koenrh)